
Autumn Good on Twitter: "Evolution of Malware Sandbox Evasion Tactics – A Retrospective Study https://t.co/XphsWFfXNo https://t.co/TTv9zgely7" / Twitter
GitHub - seifreed/awesome-sandbox-evasion: A summary about different projects/presentations/tools to test how to evade malware sandbox systems
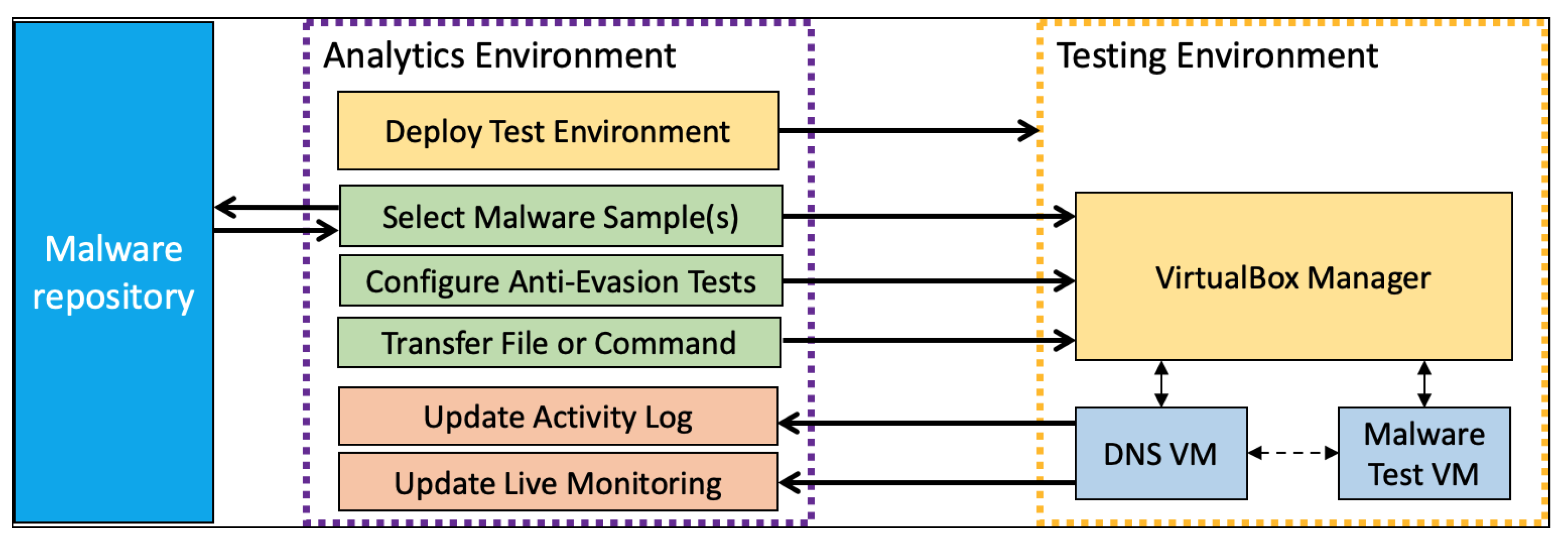



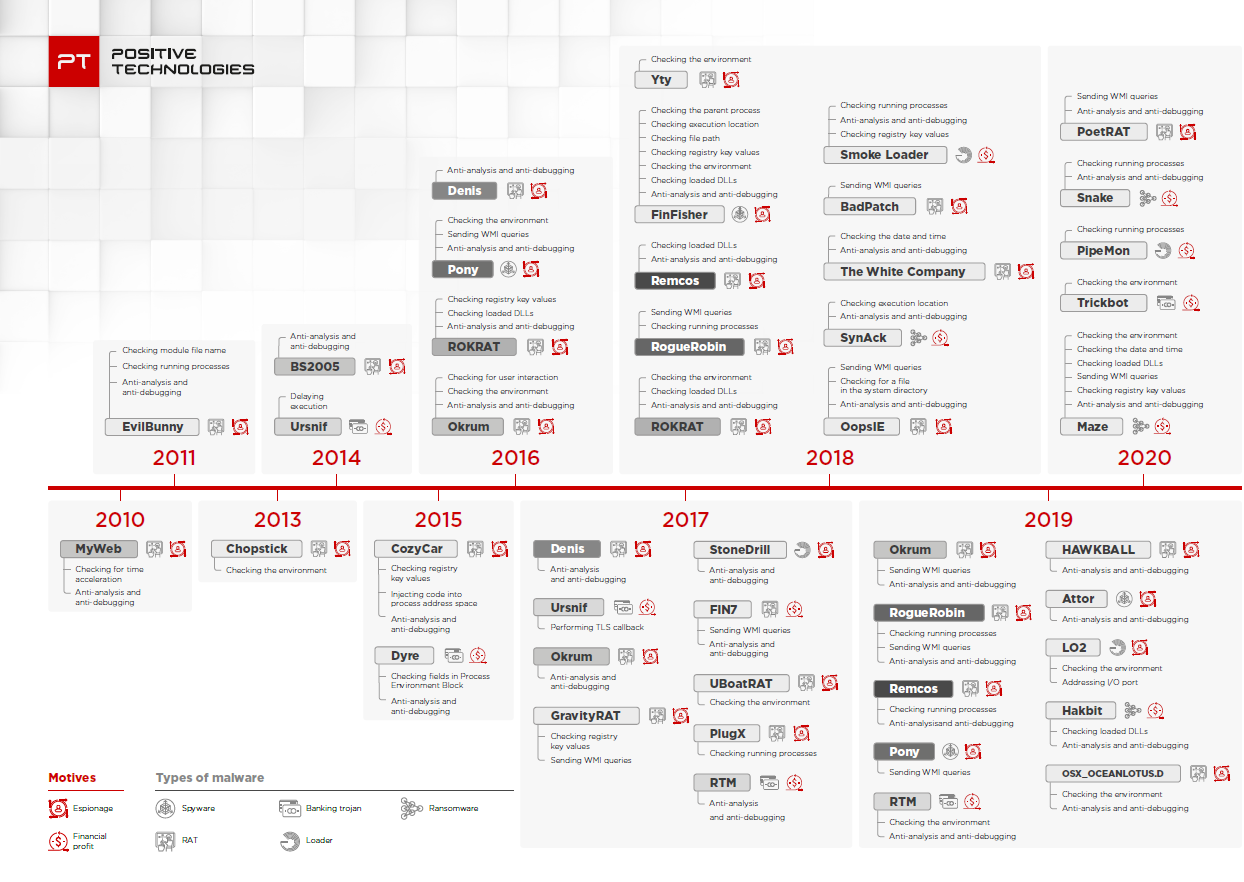













![PDF] Malware Dynamic Analysis Evasion Techniques | Semantic Scholar PDF] Malware Dynamic Analysis Evasion Techniques | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e0217797dcaf8f4c2548a2266324f0a3ac7342d6/4-Figure1-1.png)




